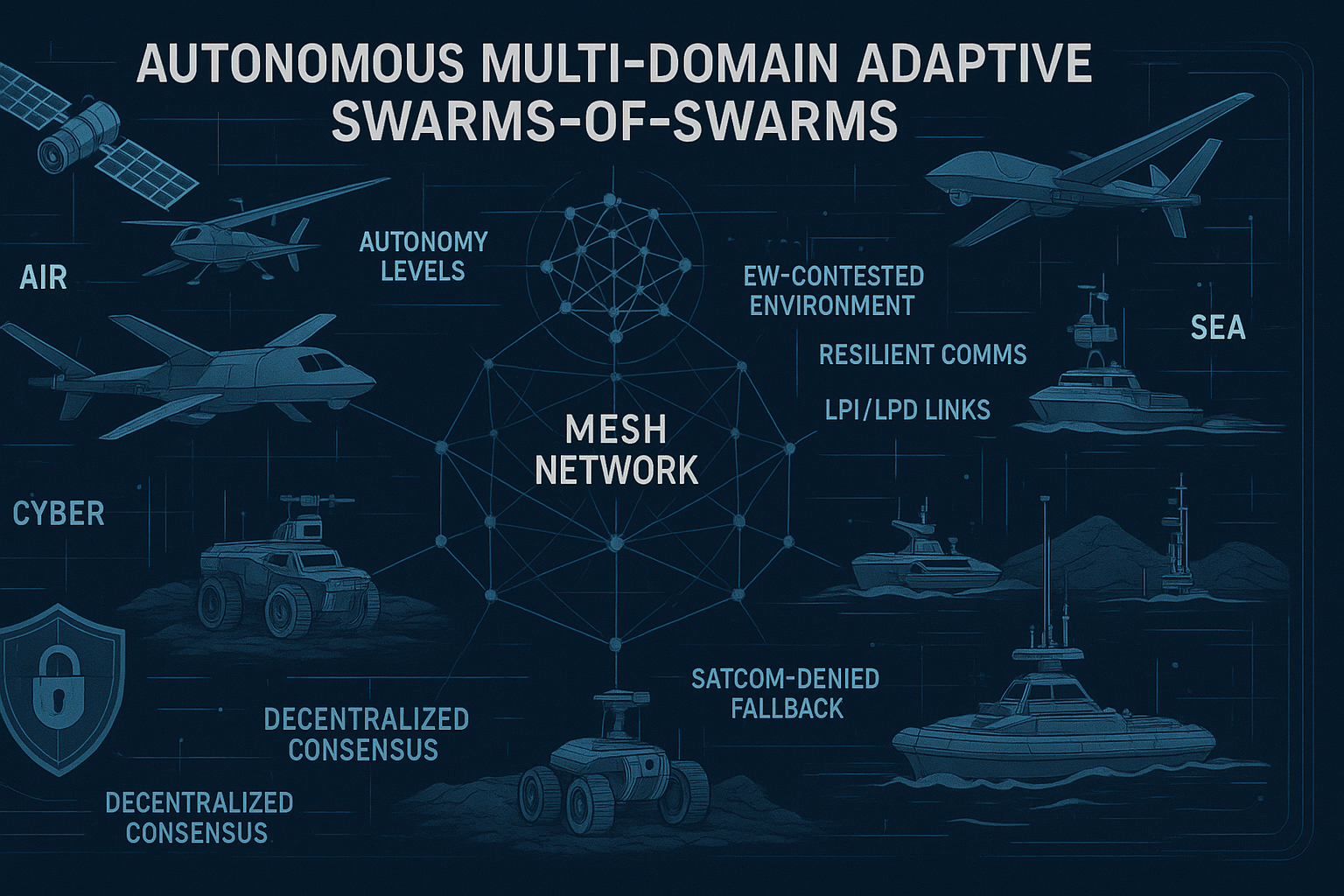
The U.S. Department of Defense’s AMASS (Autonomous Multi‑domain Adaptive Swarms‑of‑Swarms) initiative pushes adaptive swarms C2 from single‑swarm experiments toward coordinated, theater‑level orchestration across air, land, and maritime domains. By formalising requirements around common command languages, resilience, and cross‑swarm deconfliction, AMASS elevates unmanned teaming from boutique demonstrations to scalable operational architecture [1][2]. For defence primes and dual‑use innovators, the window to shape interfaces, data models, and verification methods for adaptive swarms C2 is open.

Key Facts
- Scope: AMASS seeks a scalable architecture to dynamically command and control “swarms‑of‑swarms,” coordinating heterogeneous unmanned air, ground and surface systems via a common C2 language [1][2].
- Status: The program originated as a DARPA Broad Agency Announcement (HR001123S0010) listed on SAM.gov; FY‑2024 DoD budget documents show dedicated AMASS funding and a focus on interoperable, theatre‑level effects [1][2].
- Why now: Single‑swarm control is hitting scale limits. **Adaptive swarms C2** promises graceful degradation under jamming/attrition and cross‑swarm task hand‑offs.
- Downstream: Interfaces and assurance methods set now will shape allied interoperability, export paths, and future joint exercises [2][3].
From single‑swarm control to multiswarm orchestration
Most military autonomy efforts still optimise for a single swarm under human‑on‑the‑loop supervision. Adaptive swarms C2 reframes the problem: multiple swarms—each with different vehicles, payloads, and autonomy stacks—must negotiate airspace, spectrum, tasks, and timing in contested environments. AMASS explicitly targets that higher layer, coordinating mission‑level effects with a common C2 language while tolerating node loss, communications degradation, and adversarial deception [1][2]. In short, AMASS is about stitching together swarms that were never designed to work together.
This architecture‑first shift matters because it favours open interface definitions, reference adapters, and machine‑interpretable mission products over bespoke, vendor‑locked stacks. The winners in adaptive swarms C2 will be those who can show portable behaviours, robust negotiation protocols, and verifiable safety envelopes that survive hand‑offs between heterogeneous teams.
What “adaptive” means in practice
Adaptive swarms C2 implies runtime re‑planning without human micromanagement. Three design threads stand out:
1) Hierarchical‑distributed C2
Swarm‑of‑swarms implies layered decision‑making: local behaviours at the edge, mid‑tier coordinators per swarm, and theatre‑level mission managers. The trick is pushing just enough authority downrange to avoid bottlenecks while keeping a thin supervisory layer for intent, ROE, and blue‑force deconfliction.
2) Robustness to adversarial pressure
Jamming, attrition, false targets, and GPS spoofing are not edge cases. AMASS documentation highlights dynamic reconfiguration and task reassignment after losses [2]. Expect designs to blend multi‑path comms, opportunistic mesh networking, and PNT‑hardening at the vehicle edge.
3) Assurance for emergent behaviour
Emergent effects are the point—unpredictability is not. Verification must move beyond static test scripts. Formal methods, falsification at scale, and safety cases that travel with the software stack are table stakes; DARPA’s broader autonomy portfolio points toward continuous assurance toolchains that accompany deployment [2].
“AMASS planning and execution software will enable disparate autonomous platforms to collaborate and negotiate… and dynamically adapt to attrition, targeting errors, and unanticipated adversary actions.” [2]
Procurement & industry implications
Entry points. Even without a fresh RFP, suppliers can align with the AMASS problem framing: portable behaviour libraries; adapters to translate between vendor APIs and a common C2 grammar; and high‑fidelity simulators for cross‑swarm negotiation. Early proofs that show loss‑tolerant mission completion under spectrum stress will resonate with evaluators.
Integration pathways. Expect AMASS‑style controllers to sit above existing UAS/UGV/USV stacks and to pull in legacy programmes (e.g., ground swarms, naval unmanned teams) via adapters rather than rewrites. That favours modular middleware vendors and primes that own multiple UxS lines.
Allied interoperability. Early interface choices will leak into coalition standards. If you market to NATO/EU customers, design now for coalition policy hooks (ROE, geofencing, data residency) and publish your interface contracts. Our analysis of NATO’s new sense‑and‑avoid standard shows how quickly norms harden once a reference emerges [4].
Assurance as differentiator. Competitive advantage will come from evidence: safety cases, counter‑AI threat models, and test artefacts that survive independent audit. Bring your verification graphs to the demo, not just your flight video.
Risks, limits, and sensible alternatives
Complexity tax. Over‑centralised controllers can become single points of failure; over‑distributed designs can thrash on consensus or saturate links. Keep state exchange lean; use intent‑level messaging rather than raw telemetry floods.
Adversarial ML/decoys. Adaptive swarms C2 will be attacked via data poisoning and spoofing. Bake in out‑of‑distribution detection, behaviour bounding, and provenance for mission‑critical inputs.
Human trust & policy. Even perfect autonomy fails without policy hooks. Human‑on‑the‑loop must be more than a checkbox; provide tunable autonomy levels, abort ladders, and explainable state—especially for coalition use.
Alternatives. In near‑term fielding, many forces will keep semi‑autonomous swarms with human supervisors and partitions between teams. Hybrid layering—multiple semi‑autonomous swarms coordinated by a thin mission manager—may be the practical stepping stone.
What to watch next
- Budget lines & performers. Track FY‑2024/25 documentation and contract announcements for concrete performer lists and demo venues [2].
- Exercise injects. Look for AMASS‑like controllers turning up in joint trials and service‑specific “launched effects” experiments—early signals that interface grammars are stabilising [3].
- Reference designs. Watch for open‑published grammars, negotiation protocols, and interface adapters that attract third‑party behaviours. Those will become the de facto standard for adaptive swarms C2.
- Assurance toolchains. Expect cross‑pollination from safety‑assured autonomy work into swarms (coverage metrics for emergent behaviours, compositional verification, and field telemetry‑to‑assurance feedback loops) [2].
Internal link
For adjacent standards shaping unmanned integration, see our analysis of NATO AEP‑107 sense‑and‑avoid for UAS [4].
External link
Official solicitation background: SAM.gov – AMASS (HR001123S0010) [1].
Further Reading
- AMASS origins and budget context in DoD RDT\&E FY‑2024 materials [2].
- DARPA’s prior swarm ecosystem (OFFSET) for context on human‑swarm interfaces [3].
- Doctrinal framing: a proposed, formal definition of “swarm” in U.S. doctrine [5].
References
- SAM.gov — Autonomous Multi‑domain Adaptive Swarms‑of‑Swarms (HR001123S0010)
- U.S. DoD — DARPA FY‑2024 RDT\&E Budget Justification (AMASS description and funding)
- DARPA — OFFSET (Offensive Swarm‑Enabled Tactics) program overview
- Defence Agenda — NATO AEP‑107 Sense‑and‑Avoid for UAS (internal analysis)
- U.S. Army University Press — “Defining Swarm” (2025 doctrinal proposal)
Tags: adaptive swarms C2, AMASS, multiswarm orchestration, swarm autonomy, DARPA, unmanned systems, command and control