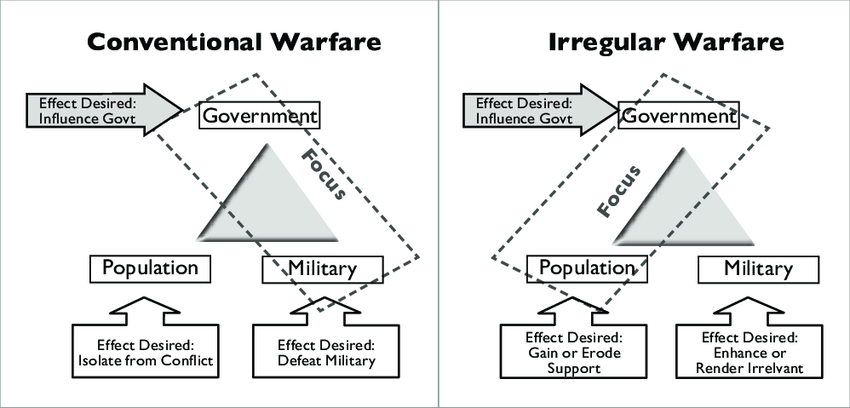
The modern competition space is digital first. As a result, it rewards the actor who can manage attribution. For irregular warfare, that shift is decisive.
In 2018, location data tied to fitness tracking helped reveal sensitive operating patterns. Later, war in Europe showed how quickly device-linked indicators can become lethal. Consequently, irregular warfare now sits at the center of strategic competition.
Key Facts
- Irregular warfare uses indirect, non-attributable, or asymmetric activities to assure or coerce.
- Digital signatures increase targeting speed, while they reduce decision time.
- Signature reduction preserves freedom of action, but it also demands governance and oversight.
Why Attribution Is Now a Strategic Variable
In strategic competition, data travels faster than people. Moreover, commercial platforms produce vast, persistent traces. That reality reshapes risk for deployed forces, partners, and proxies.
Crucially, attribution is not only a legal or political problem. Instead, it can become an operational kill chain input. Therefore, the ability to limit, manage, and interpret signatures matters.
This is where signature reduction in irregular warfare becomes essential. It is not about secrecy for its own sake. Rather, it is about sustaining tempo while protecting people and missions.
Irregular Warfare, Defined
U.S. policy defines irregular warfare as a form of warfare where state and non-state actors campaign to assure or coerce through indirect, non-attributable, or asymmetric activities. In other words, actors compete through intermediaries, influence, and tailored pressure.
Accordingly, irregular warfare does not sit “below” strategy. Instead, it often shapes the battlefield long before open conflict. It can also impose costs without triggering major escalation.
What Signature Reduction Means in Practice
Signature reduction is the disciplined effort to reduce detectable characteristics across physical and digital domains. However, it is not a single technique. Instead, it is a system: training, policy, technology, and habits.
Put simply, the goal is to preserve freedom of maneuver. At the same time, forces must comply with law, policy, and alliance commitments. Therefore, signature reduction needs governance, not improvisation.
The Strategic Case: Competition, Not Just Conflict
During major war, interceptor inventories run low. Likewise, logistics fray under repeated strikes. Consequently, human networks and local access often decide outcomes.
Yet digital exposure can neutralize human advantage. For example, adversaries can connect travel patterns, device metadata, and online behavior. Therefore, signature reduction becomes a strategic enabler for irregular warfare.
Operational Implications for SOF and the Joint Force
Operationally, signature reduction should support three outcomes. First, it should lower the probability of rapid attribution. Second, it should reduce the blast radius when attribution happens. Third, it should improve recovery and continuity after compromise.
1) Training and Standards, Not Ad Hoc Workarounds
Units need clear training standards for digital and physical signature management. Moreover, commanders need simple decision aids. As a result, teams can act quickly without guessing.
2) Command-and-Control That Survives Exposure
If communications degrade, forces still need control and accountability. Therefore, C2 must include fallback procedures. Likewise, it must include reporting pathways and auditability.
3) Partner and Proxy Risk Management
Partner forces often face the highest exposure. However, they may have the fewest defensive resources. Consequently, signature reduction should extend to the full ecosystem.
Policy Priorities: A Practical Agenda
Policymakers should treat signature reduction as an irregular warfare competency. At the same time, they must ensure oversight, ethics, and legal compliance. The right answer is balanced capability.
- Codify roles and responsibilities. Clarify who sets standards, who trains, and who audits.
- Align with information security and OPSEC. Reduce friction between policy and field reality.
- Fund secure-by-design capabilities. Prioritize tools that reduce exposure by default.
- Build allied interoperability. Ensure partners share baseline practices and incident playbooks.
- Protect civil liberties. Keep guardrails strong, especially for domestic data handling.
Finally, leaders should treat signature reduction as readiness. If a capability cannot survive digital exposure, then it is not ready.
Conclusion: Preserve Human Primacy in a Digital Age
Irregular warfare rewards access, trust, and adaptability. Meanwhile, modern technology raises the cost of being discoverable. Therefore, signature reduction is not optional.
When done well, it protects people, preserves options, and strengthens deterrence. When done poorly, it creates false confidence. The strategic task is clear: build disciplined signature reduction as a core irregular warfare function.